Which of the Following Best Describes a Memory Leak
2 A memory leak would result the program would own memory that it could no longer access. Close the Processes and Restart Your Computer.
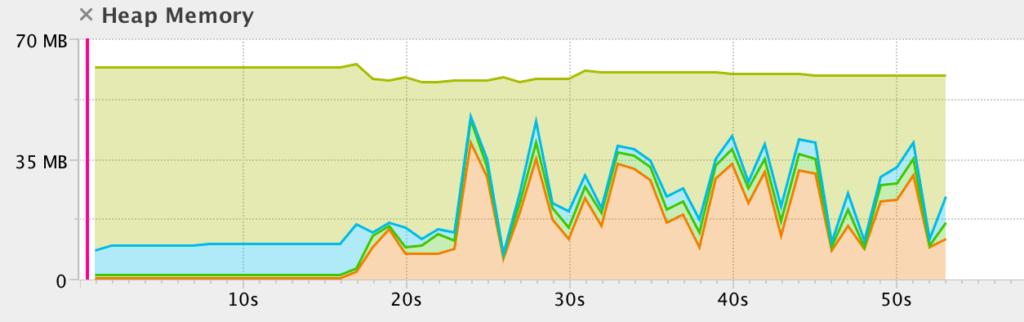
Understand And Prevent Memory Leaks In A Java Application
Which of the following best describes a collection of computers that have been compro-mised and are being controlled from one central point.

. Which of the following best describes a memory leak. Then it is not deallocated properly by programmer. Integer overflow Memory leak.
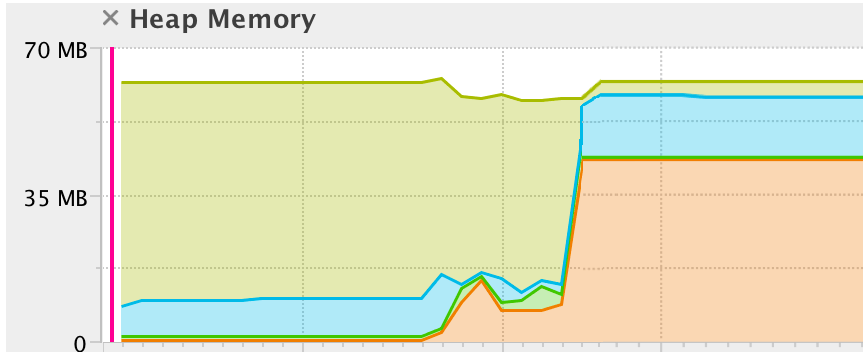
I suppose you could call it a memory leak if you want to but its distinctly different from a C-style memory leak because the object occupying the memory is still reachable and thus it can in principle be recovered at some point later in the program. The stack is cleared without the user knowing. A memory leak may cause an out-of-memory exception when memory usage increases until the process runs out of system memory or until the process stops functioning.
A memory leak may also happen when an object is stored in memory but cannot be accessed by the running code. Thats why this is called the memory leak. Planning discovery attack report B.
The L1 cache is overwritten. Heap memory allocated by the user is never freed so it is wasted. So that place is reserved for no reason.
A situation in which an application fails to properly release memory allocated to it or continually requests more memory than it needs is called. In a memory leak attack the threat actor takes advantage of the programming error of not freeing the memory after executing a process taking advantage of the devices low memory conditions to attack. Exploit escalation attack persistence.
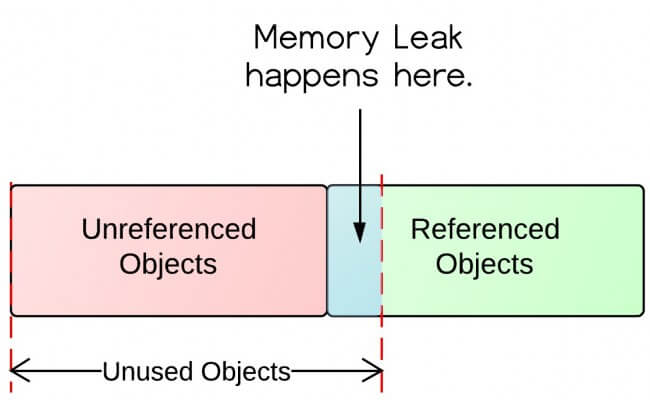
A Memory Leak is a situation when there are objects present in the heap that are no longer used but the garbage collector is unable to remove them from memory and thus they are unnecessarily maintained. Memory corruption would refer to heap or stack overflows. A situation in which an application fails to properly release memory allocated to it or continually requests more memory than it needs is called.
For the memory leak some block of memory may have wasted. Buffer overflows result from writing data beyond expected memory boundaries which can crash a program or allow arbitrary code execution. Which best describes the 4 phases of a penetration test.
Here is how to do that. Which of the following is the best practice to prevent code injection attacks. Data is written from memory to disk.
3 Both a dangling pointer and a memory leak would result. Please keep reading to get the windows 10 memory leak fix. Memory leak Which of the following terms describes an attempt to read a variable that stores a null value.
Last Updated. The CPU receives an incorrect program counter so it reads and the wrong instruction. He is currently gathering infor-.
In computer science a memory leak is a type of resource leak that occurs when a computer program incorrectly manages memory allocations in a way that memory which is no longer needed is not released. A Denial of Service. A memory leak is bad because it blocks memory resources and degrades system performance over time.
The question tells us what is happening. Eventually in the worst case too much of the available memory may become allocated and all or part of the. 1 A dangling pointer would result a pointer whose value is the address of memory that the program no longer owns.
The memory leak occurs when a piece of memory which was previously allocated by the programmer. Memory leak occurs when programmers create a memory in heap and forget to delete it. A memory leak has symptoms similar to a number of.
Which of the following describes a memory leak attack. The situation that link describes isnt a real memory leak though. That memory is no longer in use by the program.
Theres nothing in the question suggesting that multiple processes are attempting to access the same resources simultaneously a race condition. The first windows 10 memory leak fix is to close the processes in Task Manager. A memory leak simply reserves more and more memory until there is none left to assign to any other application or the OS.
Memory corruption implies changes to memory. It further tells us why. Which application-testing technique is the most likely to uncover improper input handling.
Memorybuffer vulnerability Memory leak. A defect leading to resource exhaustion of which only C Memory leak fits that descriptor. So even from the but its happening because of memory point of view memory corruption is not a valid answer.
The BizTalk Server process may be experiencing a memory leak when memory usage in Microsoft Windows Task Manager consumes more than 50 percent of the physical RAM. In a word memory leak is an issue that a program is taking up more memory than it should be. John is conducting a penetration test of a clients network.
The consequences of memory leak is that it reduces the performance of the computer by reducing the amount of available memory.
Understand And Prevent Memory Leaks In A Java Application
0 Response to "Which of the Following Best Describes a Memory Leak"
Post a Comment